New Relic Alerts (New) Integration
New Relic is the all-in-one web application performance tool that provides performance insight from the end user experience, through servers, and down to a line of application code. New Relic Alerts is New Relic's new incident management platform that offers a centralized monitoring for all New Relic products.

What does Opsgenie offer New Relic users?
Opsgenie has a native integration with New Relic Alerts. Use the integration to send New Relic incidents to Opsgenie's API with detailed information. Opsgenie acts as a dispatcher for New Relic incidents, determines the right people to notify based on on-call schedules– notifies via email, text messages (SMS), phone calls, and iPhone & Android push notifications, and escalates alerts until the alert is acknowledged or closed.
This document describes how to configure the integration and details of data that Opsgenie receives from New Relic.
Functionality of the integration
- When an alert is created in New Relic Alerts, an alert is also created in Opsgenie automatically through the integration.
- When an alert is closed in New Relic Alerts, the related alert is also closed in Opsgenie automatically through the integration.
- When an alert is acknowledged in New Relic Alerts, the related alert is also acknowledged in Opsgenie automatically through the integration.
Configuring Opsgenie side of the integration
- Please create an Opsgenie account if you haven't done so already.
- Go to Opsgenie New Relic Integration page.
For Free and Essentials plans, you can only add the integrations from the Team Dashboards, please use the alternative instructions given below to add this integration.
- Specify who is notified of New Relic incidents using the Teams field. Auto-complete suggestions are provided as you type.
An alternative for Step 2) and Step 3) is to add the integration from the Team Dashboard of the team which will own the integration. To add an integration directly to a team, navigate to the Team Dashboard and open Integrations tab. Click Add Integration and select the integration that you would like to add.
- Copy the API key.
- Click Save Integration.
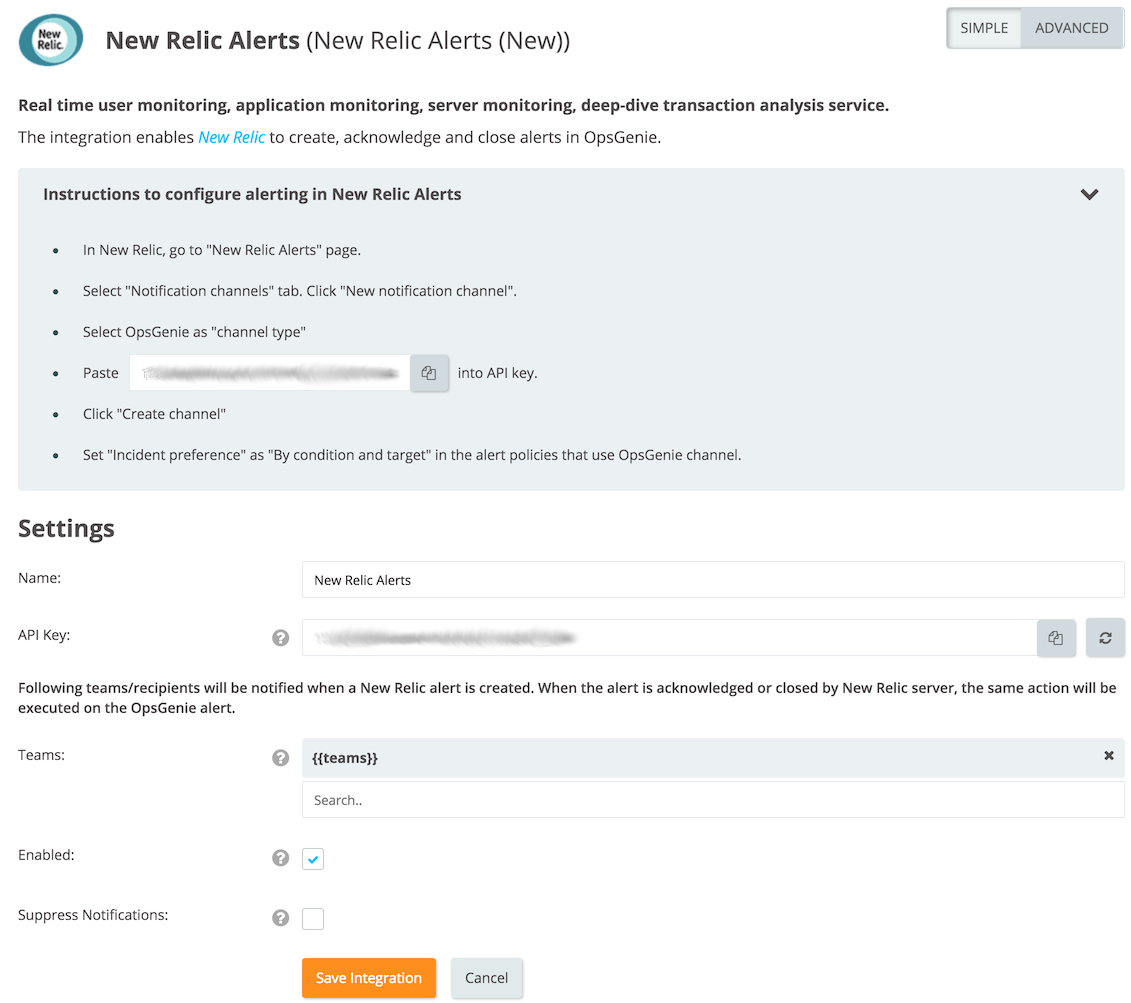
Configuring New Relic side
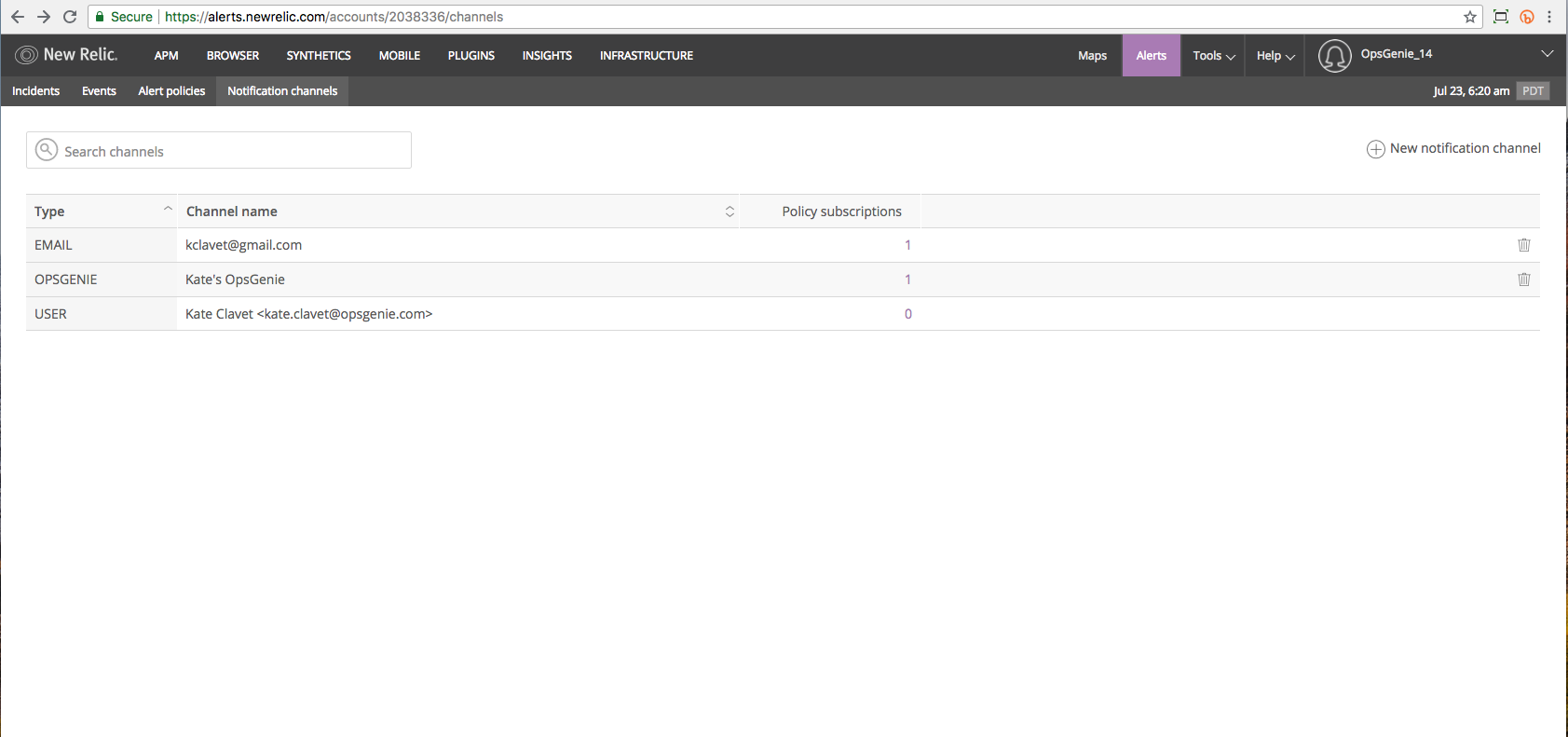
- In New Relic Alerts, select "Notification channels" tab.
- Click New notification channel.
- Select "Opsgenie".
- Paste the API key copied previously from Opsgenie into the "API key" field.
- Select the team to route alerts to and the tags to attach to the alert.
- Click "Create Channel".
7.. Click Save changes.
It's recommended to set "Incident preference" as "By condition and target" in the alert policies that use Opsgenie's channel.
- Navigate to the "Alert Policies" tab.
- Click a desired alert to set up notification channels for.
- Navigate to the "Notification Channels" tab.
- Click "Add Notification Channel"
- Select the Opsgenie channel set up in the previous steps.
All done! Now forward your New Relic incidents to Opsgenie and leverage Opsgenie's full alerting functionality.
Sample JSON payload sent from New Relic to Opsgenie
{
"tags": "tag1,tag2",
"teams": "team1,team2",
"recipients": "user1,user2",
"payload": {
"condition_id": 1,
"condition_name": "test condition",
"current_state": "open",
"details": "CPU > 50% for 5 minutes",
"event_type": "INCIDENT",
"incident_acknowledge_url": "http://localhost/incident/1/acknowledge",
"incident_api_url": "http://localhost/api/incident/1",
"incident_id": 1,
"incident_url": "http://localhost/incident/1",
"owner": "John Doe",
"policy_name": "test policy",
"policy_url": "http://localhost/policy/1",
"runbook_url": "http://localhost/runbook/url",
"severity": "CRITICAL",
"targets": [
{
"id": "12345",
"link": "http://localhost/target/12345",
"name": "Test Target",
"labels": [
"production",
"hostname"
],
"type": "Server",
"product" : "productName"
}
],
"timestamp": 123456789000
}
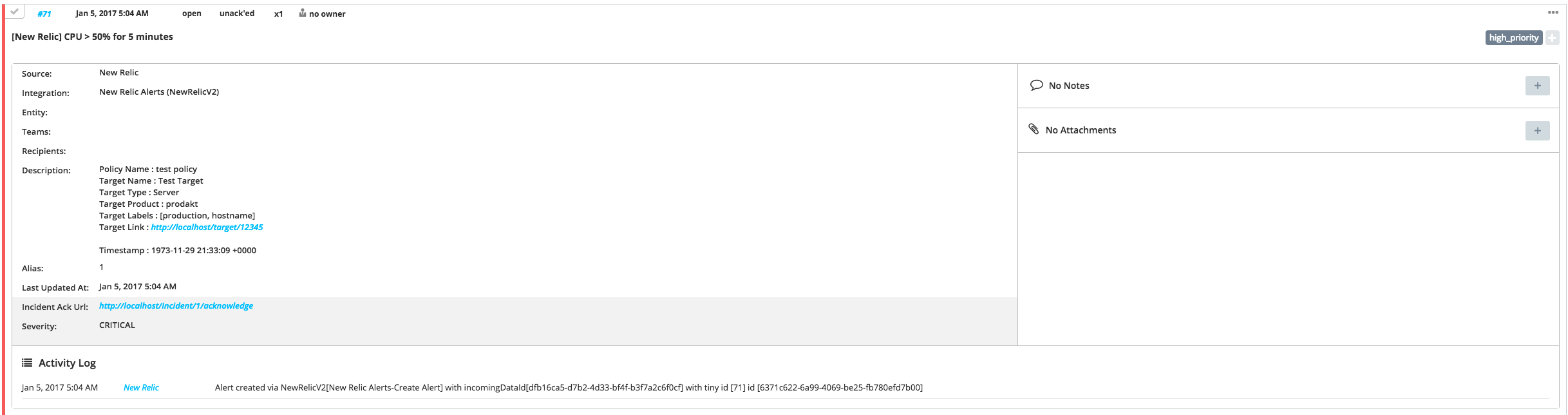
}This payload is parsed by Opsgenie as:
[
"owner" : "John Doe",
"severity" : "CRITICAL",
"policy_url" : "http://localhost/policy/1",
"teams" : [
"team1", "team2"
],
"target_name" : "Test Target",
"target_type" : "Server",
"policy_name" : "test policy",
"incident_url" : "http://localhost/incident/1",
"incident_acknowledge_url" : "http://localhost/incident/1/acknowledge",
"tags" : [
"tag1", "tag2"
],
"event_type" : "INCIDENT",
"incident_id" : "1",
"target_link" : "http://localhost/target/12345",
"runbook_url" : "http://localhost/runbook/url",
"recipients" : [
"user1", "user2"
],
"target_labels" : [
"production", "hostname"
],
"details" : "CPU > 50% for 5 minutes",
"state" : "open",
"condition_name" : "test condition",
"target_product" : "productName",
"timestamp" : "123456789000"
]Sample alert
Updated 29 days ago
