Evident.io Integration
Evident.io focuses on delivering infrastructure security for Amazon Web Services (AWS). It provides Evident Security Platform(ESP), a cloud-native solution that helps businesses detect and manage security risks of AWS infrastructure via automated threat detection, incident response, and compliance through continuous monitoring.

What does Opsgenie offer Evident.io users?
Use Opsgenie's Evident.io Integration to forward Evident.io alerts to Opsgenie. Opsgenie determines the right people to notify based on on-call schedules– notifies via email, text messages (SMS), phone calls and iOS & Android push notifications, and escalates alerts until the alert is acknowledged or closed.
Functionality of the integration
- When a signature is created in Evident.io, an alert is created in Opsgenie automatically through the integration.
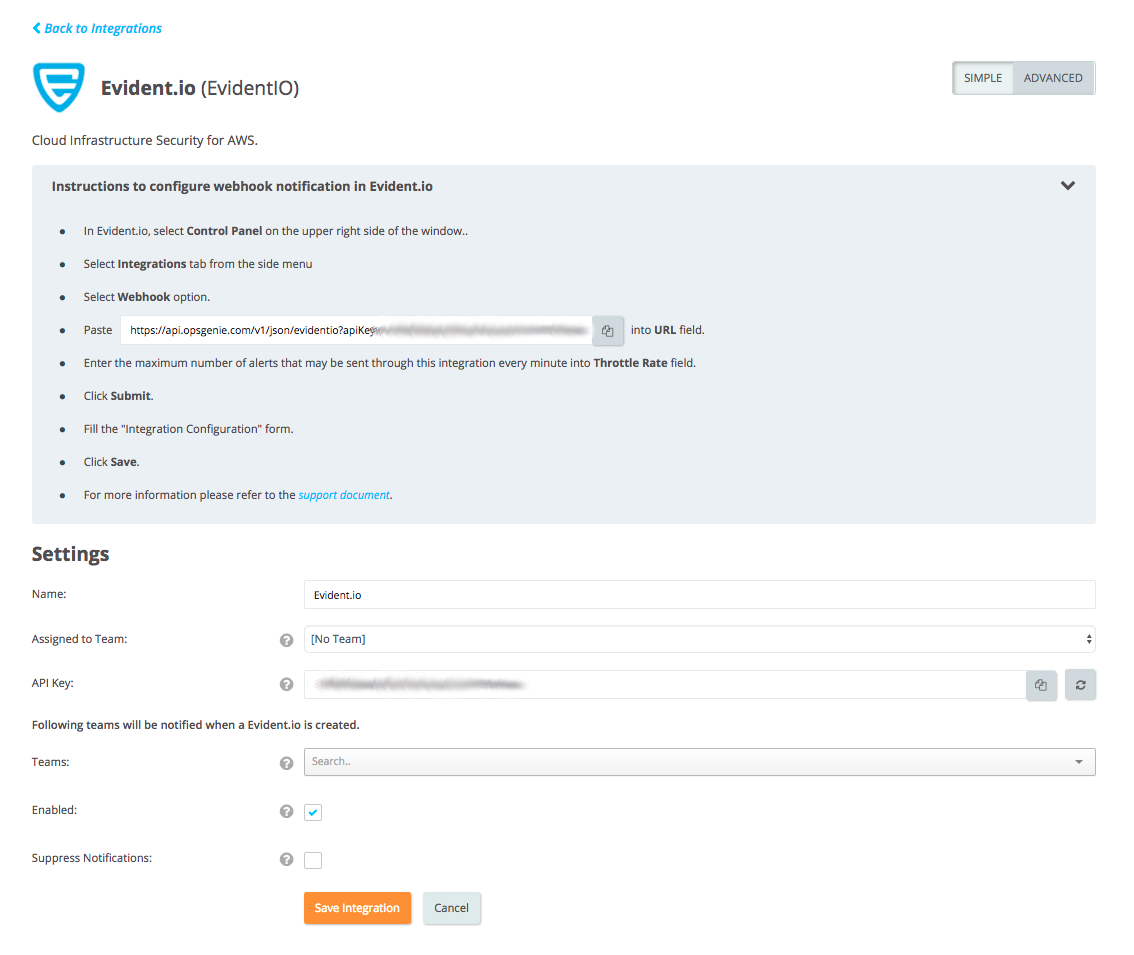
Add Evident.io Integration to Opsgenie
- Please create an Opsgenie account if you haven't done so already.
- Go to Opsgenie's Evident.io Integration page.
For Free and Essentials plans, you can only add the integrations from the Team Dashboards, please use the alternative instructions given below to add this integration.
- Specify who is notified of Evident.io alerts using the Teams field. Auto-complete suggestions are provided as you type.
An alternative for Step 2) and Step 3) is to add the integration from the Team Dashboard of the team which will own the integration. To add an integration directly to a team, navigate to the Team Dashboard and open Integrations tab. Click Add Integration and select the integration that you would like to add.
- Copy the API Key.
- Click Save Integration.
Configuration in Evident.io
- In Evident.io, select Control Panel on the upper right side of the window.
- Select the Integrations tab from the side menu.
- Select the Webhook option.

- Paste integration API URL into URL field.
- Enter the maximum number of alerts that may be sent through this integration every minute into Throttle Rate field.
- Check the alert types and signatures to receive.
- Click Submit.
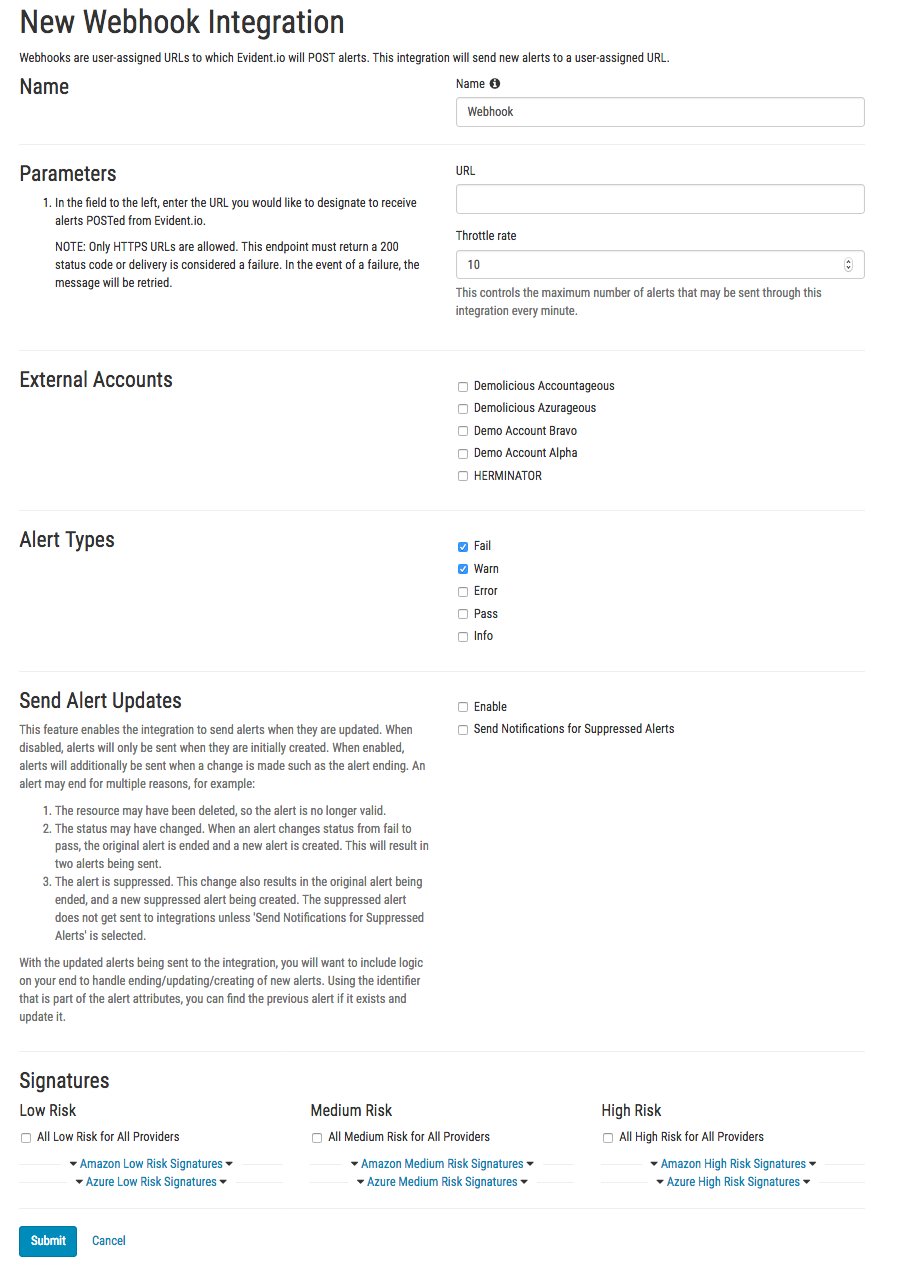
- Fill out the Integration Configuration form.
- Click Save.
Sample Webhook Message from Opsgenie Evident.io Plugin
{
"data": {
"id": "259835974",
"type": "alerts",
"attributes": {
"created_at": "2016-11-08T12:46:55.000Z",
"status": "pass",
"resource": "opsgenie-app",
"updated_at": "2016-11-09T09:45:04.000Z",
"started_at": "2016-11-08T12:46:55.000Z",
"ended_at": null
},
"relationships": {
"external_account": {
"data": {
"id": "4055",
"type": "external_accounts"
},
"links": {
"related": "https://esp.evident.io/api/v2/external_accounts/4055.json"
}
},
"region": {
"data": {
"id": "9",
"type": "regions"
},
"links": {
"related": "https://esp.evident.io/api/v2/regions/9.json"
}
},
"signature": {
"data": {
"id": "136",
"type": "signatures"
},
"links": {
"related": "https://esp.evident.io/api/v2/signatures/136.json"
}
},
"custom_signature": {
"data": null,
"links": {
"related": null
}
},
"suppression": {
"data": null,
"links": {
"related": null
}
},
"metadata": {
"data": {
"id": "258238708",
"type": "metadata"
},
"links": {
"related": "https://esp.evident.io/api/v2/alerts/259835974/metadata.json"
}
},
"cloud_trail_events": {
"data": [],
"links": {
"related": "https://esp.evident.io/api/v2/alerts/259835974/cloud_trail_events.json"
}
},
"tags": {
"data": [],
"links": {
"related": "https://esp.evident.io/api/v2/alerts/259835974/tags.json"
}
}
}
},
"included": [
{
"id": "4055",
"type": "external_accounts",
"attributes": {
"created_at": "2016-11-08T12:28:31.000Z",
"name": "OpsGenie Development",
"updated_at": "2016-11-09T06:26:22.000Z",
"arn": "arn:aws:iam::729181177740:role/Evident-Service-Role",
"account": "729181177740",
"external_id": "960f0836-b71f-45d3-a54f-4cf1608804c7",
"cloudtrail_name": null
},
"relationships": {
"organization": {
"links": {
"related": "https://esp.evident.io/api/v2/organizations/1874.json"
}
},
"sub_organization": {
"links": {
"related": "https://esp.evident.io/api/v2/sub_organizations/3426.json"
}
},
"team": {
"links": {
"related": "https://esp.evident.io/api/v2/teams/4000.json"
}
},
"scan_intervals": {
"links": {
"related": "https://esp.evident.io/api/v2/external_accounts/4055/scan_intervals.json"
}
}
}
},
{
"id": "9",
"type": "regions",
"attributes": {
"code": "global",
"created_at": "2014-06-05T23:42:37.000Z",
"updated_at": "2014-06-05T23:42:37.000Z"
}
},
{
"id": "136",
"type": "signatures",
"attributes": {
"created_at": "2016-09-07T16:30:14.000Z",
"description": "\"IAM users can access AWS resources using different types of credentials, such as passwords or access keys. Best security practice is to remove or deactivate any credentials that have been unused in the last 90 days. Disabling or removing unnecessary credentials will reduce the window of opportunity for credentials associated with a compromised or abandoned account to be used. This signature scans for any such incidents and generates a report if one is discovered.\"",
"identifier": "AWS:IAM-014",
"name": "Unused IAM User Credentials",
"resolution": "\"To resolve this alert:Open the AWS IAM Console. Go to Users, select the user identified in the alert.Select the Security Credentials tab.Click Manage Password.Click Remove Existing Password to prevent the user from logging in until their credentials can be verified.For more information: see AWS: IAM documentation.\"",
"risk_level": "Low",
"updated_at": "2016-11-01T17:17:43.000Z"
},
"relationships": {
"service": {
"links": {
"related": "https://esp.evident.io/api/v2/services/4.json"
}
}
}
},
{
"id": "258238708",
"type": "metadata",
"attributes": {
"data": {
"details": {
"arn": "arn:aws:iam::729181177740:user/opsgenie-app",
"message": "User has logged in in the past 90 days",
"username": "opsgenie-app"
}
}
}
}
]
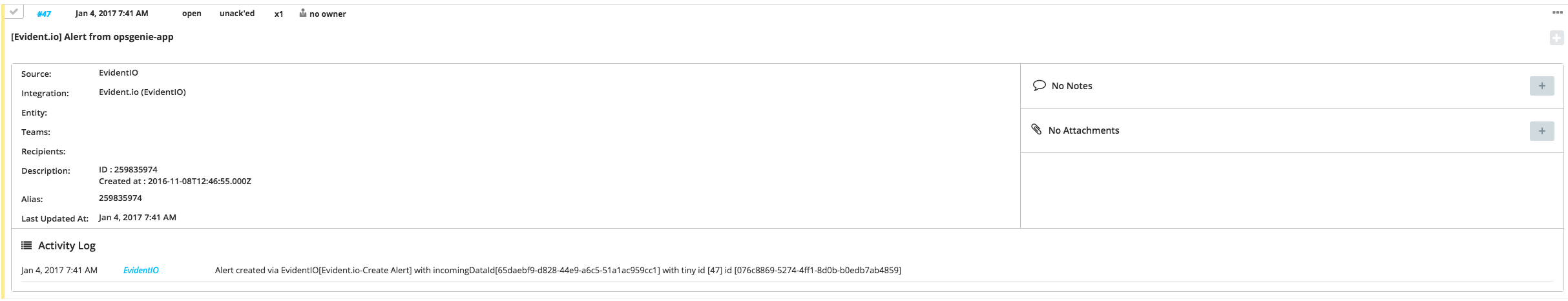
}Sample Alert
Updated 7 months ago
